Have you ever wondered how your messages in a messenger remain private? Or how an online store knows that it is you making the payment and not a fraudster? All of this is backed by an invisible but powerful force – cryptography. In today’s world, permeated by digital technologies, from secure online banking to privacy in correspondence and even functioning cryptocurrencies, cryptography plays a key role. This article is your detailed guide to the world of cryptography: we will break down its essence in simple terms, dive into its history, explore methods and algorithms, examine modern applications, learn about developments in Russia and the world, and even discuss a career in this fascinating field.
What is cryptography in simple terms
Cryptography is not just encryption; it is a whole science about methods of ensuring confidentiality, data integrity, authentication, and non-repudiation. Let’s take a closer look.
The essence and significance of cryptography
Imagine that you have a secret message that needs to be transferred to a friend in such a way that no one else can read it. You can create your own “cipher,” for example, by replacing each letter with the next one in the alphabet. This is a simple example of cryptography.
To speak more formally, cryptography (from ancient Greek κρυπτός — hidden and γράφω — to write) is the science of methods for ensuring the security of data by transforming it.
The main goals of cryptography:
- Confidentiality: The guarantee that the information is accessible only to authorized individuals. No one else should read your encrypted message.
- Data integrity: The assurance that the information has not been altered (either accidentally or intentionally) during transmission or storage.
- Authentication: Verification of the authenticity of the data source or user. How to ensure that the message came from your friend and not from an attacker?
- Non-repudiation of authorship (Non-repudiation): A guarantee that the sender will not be able to subsequently deny having sent the message or the transaction.
The importance of cryptography in the modern world is immense. Without it, secure financial operations, protected state and corporate communications, privacy of personal correspondence, and even the functioning of such innovative technologies as blockchain, smart contracts and cryptocurrencies (for example bitcoin).

Where and why it is used
Cryptography surrounds us everywhere, often working unnoticed:
- Secure websites (HTTPS): The padlock in the browser address bar means that your connection to the site is secured using cryptographic protocols (TLS/SSL), encrypting data between you and the server (logins, passwords, card details).
- Messengers: Apps like Signal, WhatsApp, and Telegram use end-to-end encryption so that only you and your correspondent can read the conversation.
- Email: PGP or S/MIME protocols allow you to encrypt messages and place digital signatures.
- Wi-Fi networks: WPA2/WPA3 protocols use cryptography to protect your home or corporate wireless network from unauthorized access.
- Bank cards: Chips on cards (EMV) use cryptographic algorithms for card authentication and transaction protection.
- Online banking and payments: All operations are protected by multilayer cryptographic systems.
- Digital signature: Used to confirm the authenticity of documents and authorship.
- Cryptocurrencies: Blockchain, the foundation of most cryptocurrencies, actively uses cryptographic hash functions and digital signatures to ensure the security, transparency, and immutability of transactions. Understanding the basics of cryptography helps to better navigate the world of digital assets.
- Data Protection: Encryption of hard drives, databases, archives to prevent information leaks.
- VPN (Virtual Private Network): Encryption of internet traffic to ensure anonymity and security when connecting through public networks.
Cryptography and encryption: what’s the difference
Although these terms are often used as synonyms, this is not entirely accurate.
- Encryption: This is the process of transforming readable information (plaintext) into an unreadable format (ciphertext) using a specific algorithm and key. Decryption is the reverse process.
- Cryptography: This is a broader scientific field, which includes not only the development and analysis of encryption algorithms but also:
- Cryptanalysis: The science of methods for breaking ciphers.
- Protocols: The development of secure means of interaction (e.g., TLS/SSL, key exchange protocols).
- Key Management: Secure creation, distribution, storage, and revocation of cryptographic keys.
- Hash Functions: Creating “digital fingerprints” of data to verify integrity.
- Digital Signatures: Methods for confirming authorship and integrity.
Thus, encryption is one of the most important tools of cryptography, but not all cryptography is limited to encryption.
The History of Cryptography
The path of cryptography spans millennia – from simple letter permutations to the most complex mathematical algorithms that underpin modern digital security.
A Brief Overview from Antiquity to the Present Day
Ancient World: The earliest known examples of encryption date back to Ancient Egypt (around 1900 BC), where non-standard hieroglyphs were used. In Ancient Sparta (5th century BC) they applied scytale – a stick of a certain diameter around which a strip of parchment was wound; the message was written along the stick, and after unwinding the strip, the letters appeared as a chaotic set. It could only be read by winding the strip around a scytale of the same diameter.
Antiquity and the Middle Ages: The famous Caesar cipher (1st century BC) – a simple shift of letters by a fixed number of positions. Arab scholars (for example, Al-Kindi, 9th century AD) made a significant contribution by developing frequency analysis – a method for breaking simple substitution ciphers by counting the frequency of letters in the ciphertext. In Europe, polyalphabetic ciphers such as Vigenère cipher (16th century) were gaining popularity and were long considered unbreakable (“le chiffre indéchiffrable”).
The Modern Era and World War I: The development of the telegraph stimulated the creation of more complex ciphers. During World War I, cryptography played an important role; for example, the breaking of the Zimmermann telegram by British cryptanalysts was one of the factors leading to the US entering the war.
World War II: This era became the golden age of mechanical cryptography. The German cipher machine “Enigma” and its breaking by the Allies (primarily Polish and British mathematicians, including Alan Turing at Bletchley Park) had a significant impact on the course of the war. The Japanese used the “Purple” machine, which was also broken by the Americans.
The Computer Era: The advent of computers revolutionized the field. In 1949, Claude Shannon published the paper “Communication Theory of Secrecy Systems”, laying the theoretical foundations of modern cryptography. In the 1970s, the DES (Data Encryption Standard) was developed. – the first widely accepted standard of symmetric encryption. In 1976, Whitfield Diffie and Martin Hellman proposed a revolutionary concept of public key cryptography, and soon the algorithm appeared RSA (Rivest, Shamir, Adleman), which is still widely used.
The iconic ciphers of the past
Wandered: An example of a transposition cipher. The secret is the diameter of the stick. Easily cracked by trial and error.
Caesar cipher: A simple substitution cipher with a shift. The key is the amount of shift (a total of 32 variants for the Russian alphabet). It is broken through brute force or frequency analysis.
Vigenère cipher: A polyalphabetic cipher that uses a keyword to determine the shift at each step. Significantly more resistant to simple frequency analysis. Broken by Charles Babbage and Friedrich Kasiski in the 19th century.
The Enigma machine: An electromechanical device with rotors, a switchboard, and a reflector. It created a very complex polyalphabetic cipher that changed with each letter. Cracking it required enormous computational (for that time) and intellectual efforts.

Transition to digital cryptography
The main difference between digital cryptography and classical cryptography is the use of mathematics and computational power. Instead of mechanical devices and manual manipulations, complex algorithms based on number theory, algebra, and probability theory have come. Key points of this transition:
Formalization: Shannon’s work provided cryptography with a rigorous mathematical foundation.
Standardization: The emergence of standards (DES, later AES) allowed for compatibility and widespread implementation of encryption.
Asymmetric cryptography: The public key concept solved the fundamental problem of securely transmitting secret keys for symmetric encryption over unsecured channels. This paved the way for secure electronic commerce, digital signatures, and secure protocols like SSL/TLS.
Increase in computing power: Allowed the use of increasingly complex and resilient algorithms, but at the same time created a threat to older ciphers.
3. Methods and algorithms of cryptography
Modern cryptography relies on complex mathematical algorithms. They can be divided into several main categories.
Symmetric and asymmetric cryptography
These are two fundamental approaches to encryption:
| Symmetric cryptography (Secret-key cryptography): | Asymmetric cryptography (Public-key cryptography): | |
| Principle | The same secret key is used for both encryption and decryption of data. | A pair of mathematically related keys is used: public and private. |
| Analogy | An ordinary lock with a key. Whoever has a key can both lock and unlock. | A mailbox with a slot. Anyone can put down a letter (encrypted with a public key), but only the owner with the key to the box (private key) can get it out and read it. |
| Advantages | Высокая скорость работы. Идеально подходит для шифрования больших объемов данных (файлы, потоковое видео, базы данных). | Solves the problem of key transfer. Allows to implement digital signature. |
| Disadvantages | The problem of securely transmitting the secret key. If the key is intercepted, the whole defence collapses. Each pair of communicating parties needs its own unique key. | Significantly slower than symmetric cryptography. Not suitable for encrypting large amounts of data directly. |
| Examples of algorithms | DES, 3DES, AES (Advanced Encryption Standard) – modern world standard, Blowfish, Twofish, GOST 28147-89 (old Russian standard), GOST R 34.12-2015 (“Grasshopper”, “Magma” – modern Russian standards). | RSA, ECC (Elliptic Curve Cryptography) – more efficient (requires a shorter key length for the same strength) and popular in modern systems, including cryptocurrencies, Diffie-Hellman (key exchange algorithm), ElGamal, GOST R 34.10-2012 (Russian digital signature standard). |
How do they work together? A hybrid approach is often used: asymmetric cryptography is applied for the secure exchange of the secret key, and then this key is used for fast encryption of the main volume of data with a symmetric algorithm. This is how HTTPS/TLS works.
Main algorithms
In addition to those mentioned, it is important to know about hash functions:
Cryptographic hash functions
These are mathematical functions that transform input data of arbitrary length into an output string of fixed length (hash, hash sum, “digital fingerprint”). Properties:
- One-wayness: It is practically impossible to recover the original data from the hash.
- Determinism: The same input always gives the same hash.
- Resistance to collisions: It is practically impossible to find two different sets of input data that produce the same hash (first type – knowing the data and the hash, one cannot find other data with the same hash; second type – one cannot find two different sets of data with the same hash).
- Avalanche Effect: The slightest change in input data leads to a radical change in the hash.
- Applications: Data integrity verification (downloaded a file – compared its hash with the published one), password storage (not the passwords themselves are stored, but their hashes), digital signatures (the document’s hash is signed), blockchain technology (linking blocks, wallet addresses).
- Examples of algorithms: MD5 (outdated, insecure), SHA-1 (outdated, insecure), SHA-2 (SHA-256, SHA-512) – widely used, SHA-3 – new standard, GOST R 34.11-2012 (“Streibog”) – Russian standard.
Quantum cryptography and its prospects
The emergence of powerful quantum computers poses a serious threat to most modern asymmetric algorithms (RSA, ECC), based on the difficulty of factoring large numbers or computing discrete logarithms. Shor’s algorithm, executed on a quantum computer, will be able to break them in a reasonable time.
In response, two directions are evolving:
Post-Quantum Cryptography (Post-Quantum Cryptography, PQC): Development of new cryptographic algorithms (both symmetric and asymmetric) that will be resistant to attacks from both classical and quantum computers. These algorithms are based on other complex mathematical problems (for example, on lattices, codes, hashes, multidimensional equations). There is an active standardization process underway (for example, the NIST competition in the USA).
Quantum cryptography: Uses principles of quantum mechanics not for computations but for protecting information.
Quantum Key Distribution (QKD): Allows two parties to create a shared secret key, while any attempt to intercept the key will inevitably change the quantum state of the transmitted particles (photons) and be detected. This is not encryption in itself but a method for securely delivering keys for classical symmetric cryptography. QKD technologies already exist and are being implemented in pilot projects.
The prospects of quantum cryptography and PQC are immense, as they will ensure data security in the future era of quantum computing.
Cryptography and steganography
These are two different techniques for hiding information:
Cryptography: Hides the content of the message, making it unreadable without a key. The mere act of transmitting an encrypted message is not concealed.
Steganography (from ancient Greek στεγανός — hidden + γράφω — I write): Hides the very existence of a secret message. The message is hidden within another, innocuous-looking object (container), for example, inside an image, audio file, video, or even text.
Cryptography and steganography can be used together: the secret message is first encrypted and then concealed in the container using steganography. This provides two layers of protection.
Modern applications of cryptography
Cryptography has become an integral part of digital infrastructure, ensuring security in various fields.
Cryptography on the internet and in messengers
TLS/SSL (Transport Layer Security / Secure Sockets Layer)
The foundation of a secure internet (HTTPS). When you see https:// and the lock icon in the browser, it means TLS/SSL is working:
- Authenticates the server (verifies its certificate).
- Establishes a secure channel through key exchange (often using asymmetric cryptography like RSA or ECC).
- Encrypts all traffic between your browser and the server (using fast symmetric algorithms like AES), protecting logins, passwords, credit card information, and other confidential information.

End-to-End Encryption (E2EE)
Used in secure messengers (Signal, WhatsApp, Threema, partially Telegram). Messages are encrypted on the sender’s device and can only be decrypted on the recipient’s device. Even the messenger provider’s server cannot read the content of the messages. Usually implemented using a combination of asymmetric and symmetric algorithms.
DNS over HTTPS (DoH) / DNS over TLS (DoT)
Encrypting DNS requests to hide from the provider or outside observers which websites you visit.
Secure email (PGP, S/MIME)
Allows for the encryption of email content and the use of digital signatures for sender authentication and integrity confirmation.
Electronic signature, banking security
Electronic (digital) signature (ES/DS)
A cryptographic mechanism that allows you to confirm authorship and the integrity of an electronic document.
How it works: A hash of the document is created, which is then encrypted with the sender’s private key. The recipient, using the sender’s public key, decrypts the hash and compares it with the hash calculated by themselves from the received document. If the hashes match, it proves that the document was signed by the owner of the private key and has not been altered after signing.
Applications: Legally significant document flow, submitting reports to government bodies, participating in electronic bidding, confirming transactions.
Banking security: Cryptography is everywhere here:
Online banking: Session protection through TLS/SSL, client database encryption, the use of multi-factor authentication with cryptographic elements (e.g., one-time passwords).
Bank cards (EMV): The card chip contains cryptographic keys and performs operations for authenticating the card with the terminal and the bank, preventing cloning.
Payment systems (Visa, Mastercard, Mir): Use complex cryptographic protocols for transaction authorization and data protection.
ATMs (ATM): Encrypting communication with the processing center, protecting PIN codes (the PIN block is encrypted).
Transaction security: The importance of cryptography is especially high when dealing with digital assets. Cryptocurrency trading platforms must provide the highest level of protection for funds and user data, using advanced cryptographic methods to protect wallets, transactions, and user accounts. Ensure that the platform you choose meets modern security standards.
Cryptography in business and government structures
Protection of corporate data: Encryption of confidential databases, documents, archives both at rest and in transit. This helps prevent damage from data breaches and comply with legal requirements (for example, GDPR, Federal Law-152 “On Personal Data”).
Secure communication: Using VPNs for secure remote access for employees to the corporate network, encrypting corporate email and instant messaging.
Secure document management: Implementing electronic document management systems (EDMS) using electronic signatures to give documents legal force and ensure their integrity and authorship.
State secrets and secure communication: Government structures use certified cryptographic means to protect confidential information and ensure secure communication between agencies.
Access management systems: Cryptographic methods (e.g., tokens, smart cards) are used for user authentication and managing their access rights to information systems and physical objects.
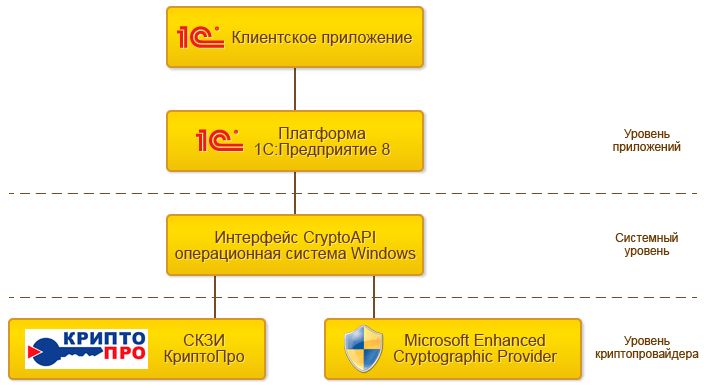
Cryptography in Russian Corporate systems (1C)
In Russia, the popular platform “1C:Enterprise” and other corporate systems are often integrated with cryptographic information protection means (CIPM), such as CryptoPro CSP or VipNet CSP. This is necessary for:
Submitting electronic reports: The formation and submission of tax, accounting, and other reports to regulatory authorities (FNS, PFR, FSS) requires the use of a qualified electronic signature.
Electronic document flow (EDF): Exchange of legally significant documents (invoices, acts, contracts) with counterparties through EDF operators.
Participation in government procurement: Working on electronic trading platforms (ETP) requires an electronic signature.
Data protection: Some configurations of 1C and other systems can use cryptographic means of protecting information (CMI) for encrypting databases or individual records.
Integration with CMI allows compliance with Russian legislation and ensures the security of business processes directly from the familiar interface of the corporate system.
Cryptography in the world
The development and regulation of cryptography have their peculiarities in different countries, but general trends and international cooperation also play an important role.
Russian achievements and cryptography services (FSB, GOST)
Russia has a long and strong history in the field of cryptography, rooted in the Soviet mathematical school.
Historical context: Soviet mathematicians made significant contributions to coding theory and cryptography, although many developments remained classified for a long time:
State standards (GOST): Russia has its own cryptographic standards developed and approved by the state. Key active standards:
- GOST R 34.12-2015: Standard for symmetric block encryption, including two algorithms – ‘Kuznetschik’ (128 bits) and ‘Magma’ (64 bits, development of the old GOST 28147-89).
- GOST R 34.10-2012: Standard for algorithms for the formation and verification of electronic digital signatures based on elliptic curves.
- GOST R 34.11-2012: The standard of the cryptographic hash algorithm “Streebog” (with a hash length of 256 or 512 bits). The use of GOSTs is mandatory for protecting information in state information systems, when working with state secrets, and is often required for interaction with government bodies (for example, when using qualified electronic signatures).
Regulatory authorities. A key role in regulating cryptography in Russia is played by:
- FSB of Russia (Federal Security Service): It licenses activities in the field of development, production, distribution, and maintenance of encryption (cryptographic) tools, as well as certifies these tools for compliance with security requirements. The FSB also approves cryptographic standards.
- FSTEC of Russia (Federal Service for Technical and Export Control): Regulates issues of technical information protection, including non-cryptographic methods, but its activities are closely related to cryptography within the framework of comprehensive protection.
Russian developers: There are a number of companies in the country specializing in the development of cryptographic information protection tools and solutions in the field of information security (for example, CryptoPro, InfoTeKS, Code of Security)
USA: Historically one of the leaders in cryptography.
- NIST (National Institute of Standards and Technology): Plays a key role in the standardization of cryptographic algorithms used worldwide (DES, AES, SHA series). Currently conducting a competition to select post-quantum cryptography standards.
- NSA (National Security Agency): Historically involved in the development and analysis of cryptography, sometimes causing controversy over possible influence on standards.
Strong academic school and private sector: Many universities and technology companies are conducting advanced research.
Europe: Actively developing its own expertise and standards.
- ENISA (European Union Agency for Cybersecurity): EU cybersecurity agency promoting best practices and standards.
- GDPR (General Data Protection Regulation): Although it does not directly prescribe specific algorithms, it requires the adoption of adequate technical measures to protect personal data, where encryption plays an important role.
National centers: Countries such as Germany, France, and the United Kingdom have strong national cybersecurity centers and cryptographic traditions.
China: Aiming for technological sovereignty in cryptography.
Proprietary standards: Develops and promotes its national cryptographic algorithms (for example, SM2, SM3, SM4).
State control: Strict regulation of the use of cryptography within the country.
Active research: Significant investments in research, including in quantum technologies and post-quantum cryptography.
International cryptography standards
In addition to national standards (GOST, NIST, Chinese SM), there are also international ones:
- ISO/IEC (International Organization for Standardization / International Electrotechnical Commission): Develops standards in the field of information technology and security, including cryptography (for example, ISO/IEC 18033 standard – encryption, ISO/IEC 9797 – MAC codes, ISO/IEC 11770 – key management).
- IETF (Internet Engineering Task Force): Develops standards for the internet, including cryptographic protocols (TLS, IPsec, PGP).
- IEEE (Institute of Electrical and Electronics Engineers): Standardizes cryptographic aspects in network technologies (for example, in Wi-Fi standards).
Although national standards are important, international standards ensure compatibility and trust in global communication and trade systems.
Cryptography as a profession
As the world’s dependence on digital technologies grows, the demand for specialists in cryptography and information security is constantly increasing.
In-demand professions and skills
Specialists whose work is related to cryptography can hold various positions:
Cryptographer (researcher): Engaged in the development of new cryptographic algorithms and protocols, analyzing their robustness, researching in the field of post-quantum cryptography. Requires deep knowledge of mathematics (number theory, algebra, probability theory, complexity theory).
Cryptanalyst: Specializes in the analysis and hacking of existing encryption and cryptosystems. Works both on the ‘defense side’ (seeking vulnerabilities for their elimination) and in special services.
Information Security Engineer / Information Security Specialist: Applies cryptographic tools in practice to protect systems and data. Engages in the implementation and configuration of cryptographic protection systems, VPN, PKI (public key infrastructure), encryption systems, key management, and security monitoring.
Secure Software Developer: A programmer who understands cryptography and knows how to properly use cryptographic libraries and APIs to create secure applications.
Pentester (Penetration Testing Specialist): Searches for vulnerabilities in systems, including the misuse of cryptography, for subsequent remediation.
Key skills:
- Fundamental knowledge of mathematics.
- Understanding of how cryptographic algorithms and protocols work.
- Programming skills (Python, C++, Java are often in demand).
- Knowledge of networking technologies and protocols.
- Understanding of operating systems.
- Analytical thinking, ability to solve non-standard tasks.
- Attention to detail.
- Continuous self-education (the field is rapidly evolving).
Where to study cryptography
You can get an education in the field of cryptography in various educational institutions:
Universities: Many leading global universities (MIT, Stanford, ETH Zurich, EPFL, Technion, etc.) have strong programs and research groups in the field of cryptography and cybersecurity.
Online platforms: Coursera, edX, and Udacity offer courses from leading professors and universities around the world.
Work and career in the field of information security
A career in cybersecurity and cryptography offers many paths:
Sectors: IT companies, fintech (banks, payment systems, cryptocurrency platforms – exchanges), telecommunications companies, government bodies (intelligence agencies, regulators), defense industry, consulting companies (cybersecurity audit, pentesting), large corporations in any industry.
Growth: Typically starting from junior specialist/engineer positions, with experience you can progress to senior specialist, head of the cybersecurity department, security architect, consultant, or move into research.
Demand: The demand for qualified cybersecurity specialists remains consistently high and continues to grow due to increasing cyber threats and digitalization.
Salaries: Salary levels in the field of cybersecurity are generally above the average of the IT market, especially for experienced specialists with deep knowledge of cryptography.
This is a dynamic and intellectually stimulating field that requires continuous development, but offers interesting challenges and good career prospects.
Conclusion
Cryptography is not just a set of complex formulas; it is a fundamental technology that ensures trust and security in our increasingly digital world. From protecting personal correspondence and financial transactions to powering government systems and cutting-edge technologies like blockchain, its impact is immense. We traced its journey from ancient wanderings to quantum computing, examined the main methods and algorithms, and observed its application in Russia and abroad.
Understanding the basics of cryptography is becoming an important skill not only for cybersecurity specialists but also for any user who wants to approach the protection of their data online with awareness. The development of cryptography continues; new challenges (quantum computers) and new solutions (post-quantum algorithms, QKD) are emerging. This dynamic field of science and technology will continue to shape a secure digital future. We hope this article has helped you better understand the world of cryptography and its significance. Take care of your digital security and use reliable tools and crypto platforms for your online activities.
Answers to frequently asked questions (FAQ)
What to do in case of a cryptography error?
What to do when encountering a cryptography error? “Cryptography error” is a general message that can occur in various situations (when working with electronic signatures, connecting to a site, using cryptographic hardware). The causes can be diverse: for example, issues with the certificate (it has expired)
What to do: Restart the program or computer.
Check the expiration date of the certificate and its status.
Update the cryptographic hardware, browser, operating system.
Check the settings of the cryptographic hardware according to the instructions.
Try using another browser (if the error occurs in it).
Refer to the documentation of the software being used or contact technical support.
If it concerns an electronic signature, contact the certification authority that issued the signature.
What is a cryptographic module?
A cryptographic module is a hardware or software component specifically designed to perform cryptographic operations (encryption, decryption, key generation, hash computation, creating and verifying electronic signatures).
Lessons on cryptography for schoolchildren and students. Where to find them?
Study history: Caesar ciphers, Vigenère ciphers – a great start to understanding the basic principles.
Solve problems and puzzles: There are online platforms with cryptographic tasks of varying difficulty (for example, CryptoHack, CTF competitions).
Read popular science literature: Books by Simon Singh (“The Code Book”) or Bruce Schneier (“Applied Cryptography” – more complex) may be interesting.
Visit the Cryptography Museum (if possible).
Study mathematics: Algebra, number theory, probability theory – the foundation of cryptography.
Simple programs: Try to implement simple ciphers (Caesar, Vigenère) in any programming language.
Online courses for beginners: Introductory courses are available on Coursera, Stepik, and other platforms.
Join MEXC and Get up to $10,000 Bonus!
Sign Up


