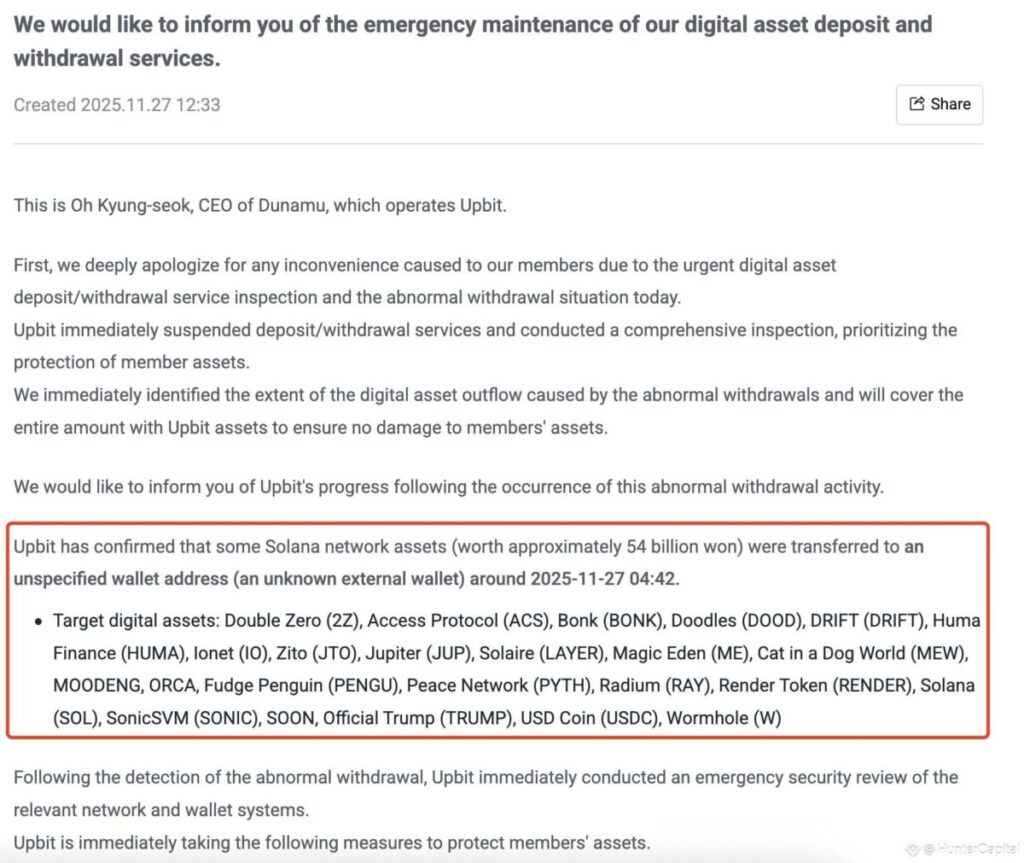
At dawn on November 27, the Korean crypto community was stunned when Upbit – the country’s largest exchange – unexpectedly activated emergency maintenance mode after detecting a series of unusual transactions on the Solana network. Within just a few minutes, multiple hot wallets belonging to the exchange simultaneously transferred assets to a completely unfamiliar address, raising suspicions of a deliberate attack. Dozens of tokens — from well-known names like BONK, PYTH, JUP to lesser-known assets — “vanished” from the system without any legitimate withdrawal requests.

1. Context: The incident occurred at a sensitive time
Upbit has long been considered the “fortress” of the South Korean crypto market, accounting for over 70% of the country’s total trading volume. However, despite numerous warnings about the risks associated with hot wallets on CeFi exchanges, Upbit’s system still has to operate with large amounts of assets to meet instant deposit–withdrawal demands. In particular, the Solana network has recently witnessed explosive growth in meme tokens and DeFi activity, causing transaction volume on the exchange’s Solana hot wallets to surge. Amid this bustling network activity, the early-morning incident on November 27 struck like an unexpected blow.
2. Attack timeline: A series of abnormal transactions emerged
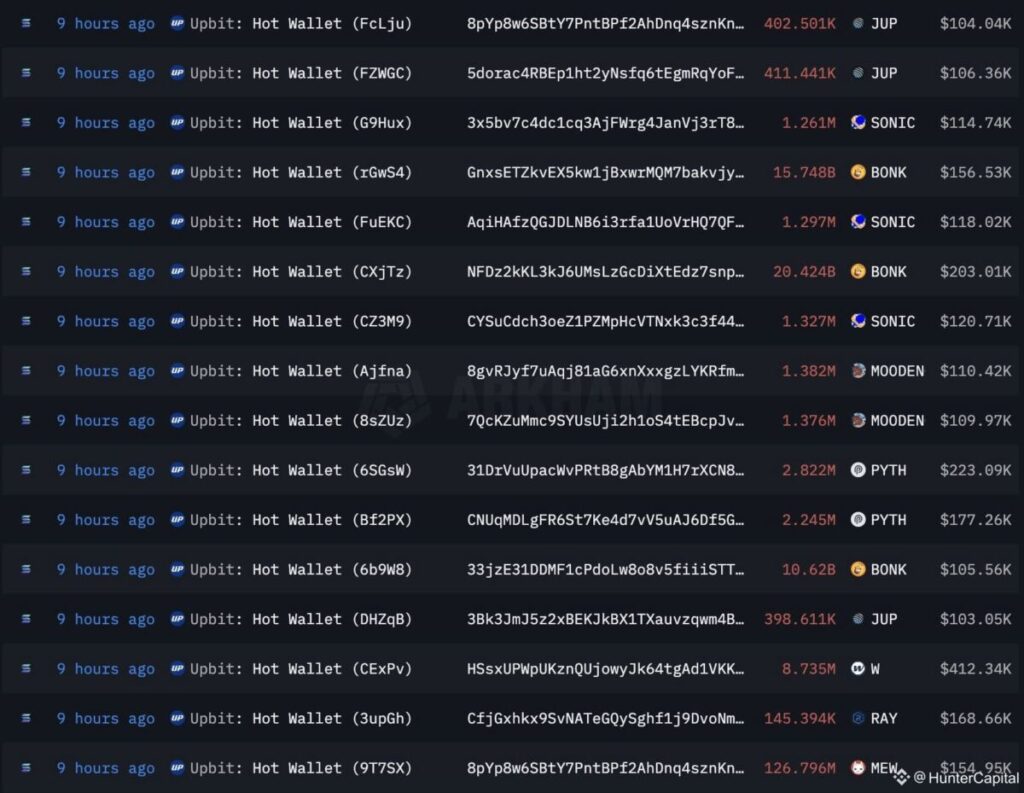
At around 4:42 AM, Upbit’s monitoring system detected a series of asset transfer requests from several hot wallets connected to the Solana network. The transactions displayed a very distinctive pattern: large yet consistent token amounts, executed over a short time window, and all funneled into a wallet address that does not belong to the exchange’s official custody infrastructure.
Millions of BONK tokens, hundreds of thousands of JUP, PYTH, SONIC, and many other long-tail assets were drained from the hot wallets within just minutes. On-chain data shows that these transactions did not follow the normal withdrawal procedure, which typically requires user authentication and internal verification. This raised strong suspicion that the hacker either gained control of the private keys or directly compromised Upbit’s automated transaction-signing system.
3. Upbit’s response: Activating emergency mode and reassuring users
As soon as the abnormal fund movements were identified, Upbit immediately shut down all deposit and withdrawal functions for Solana-based assets and transferred the remaining funds from hot wallets to cold storage to prevent further damage.
By noon the same day, CEO Oh Kyung-seok officially confirmed that a security breach had occurred, published a list of affected tokens, and pledged that all losses would be fully compensated by Upbit’s own reserve funds. This was a strong move intended to prevent panic or a withdrawal wave in the Korean market, which is highly sensitive to security-related news.
Upbit also issued an apology to users and stated that it is working with South Korea’s cybersecurity authorities to investigate the origin of the attack.
4. Security analysis: The vulnerability likely lies in the Solana hot wallet
The incident shows multiple signs of an attack targeting the infrastructure layer rather than a smart contract flaw:
Possibility 1: Private key leakage
If the hacker obtained the private key of Upbit’s Solana hot wallet, they could sign arbitrary transactions without bypassing any additional security layers.
Possibility 2: Compromise of the automated transaction-signing system
Large exchanges typically use internal signing systems. If the server or signing module is compromised, the attacker can generate a stream of “valid” transactions from the blockchain’s perspective.
Possibility 3: Exploitation of a withdrawal API
If an internal endpoint was leaked or misconfigured, the attacker might send withdrawal requests that bypass internal review.
Common thread
All three scenarios indicate a deliberate and highly informed attack that understood the exchange’s operational structure — not user error or a random technical mishap.
5. Market impact: Panic sentiment and short-term volatility
The incident at Upbit immediately triggered a ripple effect across the Korean trading community—one of the most influential crypto markets in Asia. In the first few hours after the emergency maintenance announcement, many Solana-based tokens experienced unusual price fluctuations as investors grew concerned about potential mass sell-offs or prolonged trading suspensions.
Tokens such as BONK, PYTH, and JUP — which were withdrawn in large amounts — recorded a sudden surge in trading volume across both CEXs and DEXs. However, thanks to Upbit’s quick reassurance and commitment to full compensation, the downturn did not escalate into a widespread “panic sell.”
On a global level, the Solana market reacted more cautiously. International investors recognized that the incident stemmed from Upbit’s internal systems rather than any vulnerability in the Solana blockchain itself. Therefore, the long-term impact on the broader Solana ecosystem is expected to be limited.
6. Likely movements of the hacker’s wallet: Common post-attack behavior
In typical hot-wallet hacks, attackers often take the following steps:
Split tokens into multiple secondary wallets They divide the stolen assets into smaller portions to reduce traceability and prepare for the next step: token swapping.
Swap tokens to obfuscate the fund flow The hacker may convert the Solana-based tokens into SOL, stablecoins, or high-liquidity assets on DEXs such as Orca or Raydium. The goal is to minimize the risk of freezing and make tracking more difficult.
Use a bridge to move funds to another blockchain Especially Ethereum or other bridges with lighter monitoring. Once the assets leave Solana, tracking becomes significantly harder.
Use mixers or obfuscation services If they manage to move funds to Ethereum, they might use Tornado Cash or other on-chain obfuscation techniques.
In Upbit’s case, many of the stolen tokens are long-tail with low liquidity. This poses a major risk of price slippage for the hacker if they attempt to sell quickly. This factor may actually assist investigators in tracing the attacker if they haven’t already diversified the assets.
7. Risks for Solana tokens: Temporary pressure on the ecosystem
Although the incident occurred at Upbit — not on Solana itself — the ecosystem still faces several short-term risks:
Sell pressure from the hacker If the attacker tries to liquidate the stolen tokens, long-tail assets will face heavy downward pressure due to their low liquidity.
Liquidity disruption at Upbit Upbit handles a large volume of Solana token trading, especially those listed for the Korean market. Temporary trading suspension disrupts flow and creates short-term pressure.
Spillover fear affecting other exchanges Other CeFi platforms like Bithumb or Coinone might increase preventive maintenance, causing withdrawal delays for Solana assets.
Korean retail investors pausing Solana-related trading Users may limit trading of Solana-linked tokens until Upbit fully restores deposit and withdrawal services.
However, these risks are short-term and manageable since the issue originates from Upbit’s internal operations, not the Solana blockchain.
8. Conclusion: A wake-up call for hot-wallet security across exchanges
The early-morning attack on November 27 is a powerful reminder that even major exchanges like Upbit remain vulnerable to hot-wallet risks. CeFi platforms, in their effort to optimize withdrawal speed, often sacrifice part of their security by keeping large assets in hot wallets.
This incident did not stem from the Solana blockchain; instead, it originated from Upbit’s internal systems — potentially due to private key exposure, API vulnerabilities, or a compromised signing module. On the positive side, Upbit responded swiftly, limited further damage, and maintained user trust through its full-compensation pledge.
In the coming period, this attack will likely force exchanges across Korea and Asia to re-evaluate their hot-wallet architecture, especially on high-throughput networks like Solana. It may serve as a catalyst pushing exchanges toward more advanced security models, reducing reliance on simple private keys and increasing adoption of multi-sig or MPC solutions. Disclaimer:The information provided here is for informational purposes only and should not be considered financial, investment, legal, or professional advice. Always conduct your own research, consider your financial situation, and, if necessary, consult with a licensed professional before making any decisions.
Join MEXC and Get up to $10,000 Bonus!
Sign Up


